MDT 2013 Guide 01: Intro and Active Directory Setup
This will be a guide to installing MDT 2013 and using that to deploy Windows 8.1 to a workstation. The guide is intended to be a framework that can be customised for your specific organisation or home lab.
All the machines I reference (both servers and workstations) are virtual machines running on a single VMware ESXi host in my home lab. The same instructions will work on other virtualisation platforms such as Hyper-V or Virtualbox.
Prerequisites
Virtual Machines:
- A domain controller. Any version of Windows Server would work, but I recommend at least Server 2008. This can be a minimal setup, as long as the domain controller runs the following:
- Active Directory
- DNS
- DHCP scope
- For the purposes of this guide, I use Windows Server 2012 R2, as it’s the latest evaluation edition that can be downloaded.
- If you need any help setting up the domain controller, you can follow the instructions in Part 5 and Part 6 of my Lab-in-a-Box series.
- A separate virtual machine set up as the MDT server, joined to the above domain. Again, any Windows Server version from 2008 onwards would be fine.
- The server only needs to be joined to the domain. We will perform all other installations and configuration later in this guide..
- This server requires internet access in order to configure WSUS.
- As best practice I recommend adding a second larger hard drive to store all the software and OS images.
- A separate virtual machine to use for the Windows 8.1 Gold Image.
- A separate virtual machine to test deployment of the Gold Image onto a regular workstation.
These workstation VMs should have nothing installed on them (blank hard drives). You will need to note down the MAC address of each workstation, for use when configuring the MDT Database.
Software:
The following software will be used in this guide:
- MDT 2013
- ADK for Windows 8.1
- SQL Server 2012 Express – pick the version which includes the Management Tools (SQLEXPRWT_x64_ENU.exe)
- Windows 8.1 Enterprise Evaluation – download the 64-bit version
- Microsoft Office 2013 Professional – download the 32-bit version
I suggest starting the downloads now while reading the rest of the guide, as they can take a while.
Active Directory Setup
Before we install any of the software, we’ll configure some users and groups in AD to deal with the various permissions required for MDT, and we’ll set up a GPO to configure some settings.
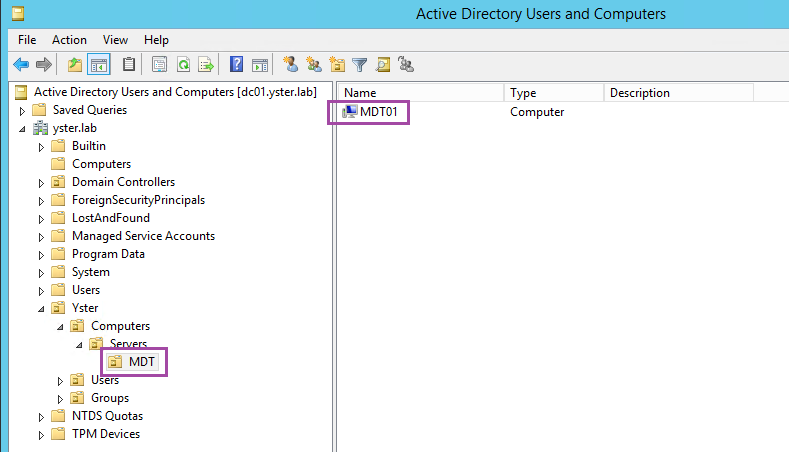
MDT Server OU
On the domain controller, open Active Directory Users and Computers. If you don’t already have an OU set up for your MDT servers, I recommend creating one and moving your MDT server into this OU. In my lab, I’ve done as follows:
This will be used later when we set up the GPO for the MDT servers.
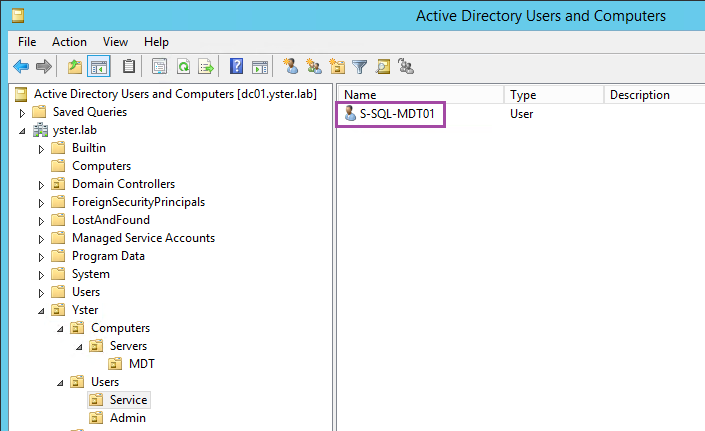
SQL Service Account
Since we’ll be installing SQL Server on the MDT server, I create a separate Service Account for the SQL service. This account is simply a regular domain user with a complex password. I use a specific naming convention to denote that it’s a service account for SQL on my MDT01 server, but you can name it anything.
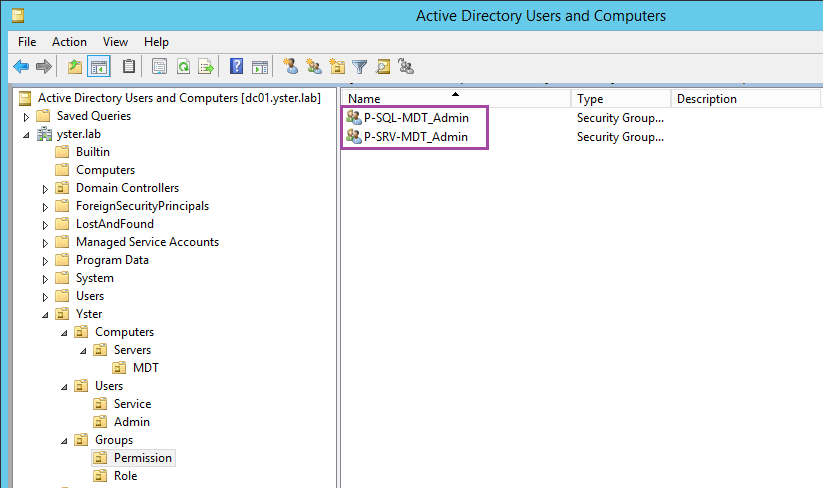
Role and Permission Groups
I also follow a Role Based Access Control system whenever possible, so I create some Role and Permission groups for use by the GPO and when installing SQL Server. These are regular Global Security groups, created by right-clicking the OU and choosing New – Group.
Firstly, I create a group for Local Administrator permission on the server – P-SRV-MDT_Admin. Secondly, I create a group for SQL Administrator permissions on the server – P-SQL-MDT_Admin.
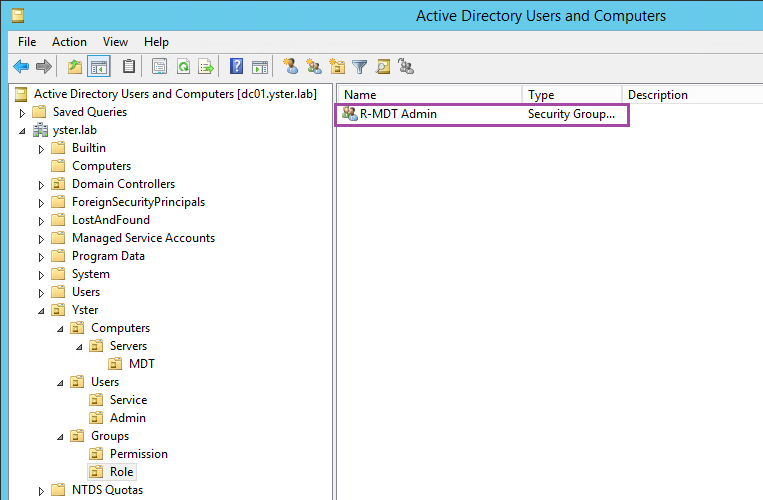
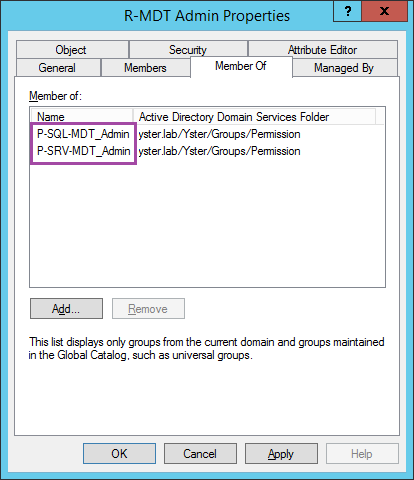
Next I’ll create a Role group, for all MDT administrators. In the Roles OU, create the group R-MDT Admin.
Go to the properties of that group, and select the Members tab. Add your own user account (or Administrator, if you’re using that) to the Members. Select the Member Of tab and add the two Permission groups you created above.
This ensures that your login account is part of the “MDT Admin” Role group, and that the Role group has “Local Admin” and “SQL Admin” permissions on the server.
MDT Server GPO
Next we will configure a Group Policy Object (GPO) to do the following for the MDT server:
- Add the above MDT “Local Admin” group to the local Administrators group on the server.
- Open the Windows Firewall to allow connections to the SQL server from other computers. This will allow computers to query the SQL database during their build task sequence.
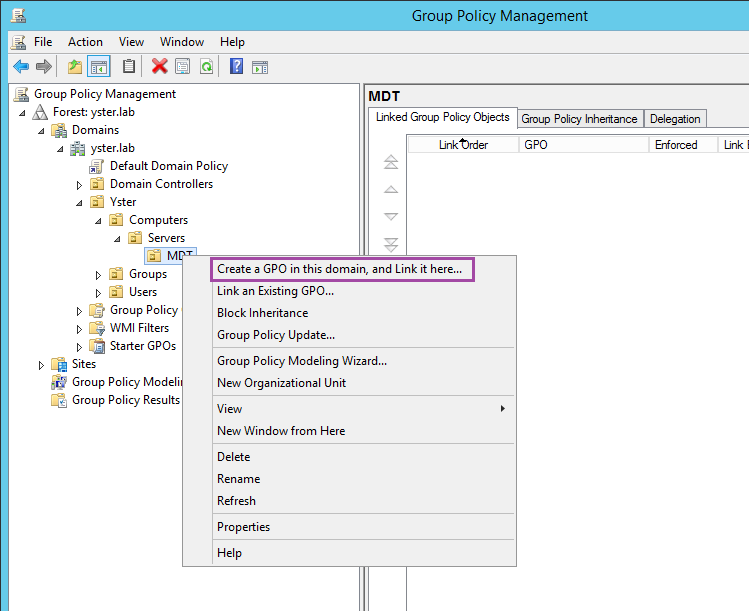
Open Group Policy Management. Drill down to the OU containing your MDT server, right-click on the OU and choose Create a GPO in this domain, and Link it here…
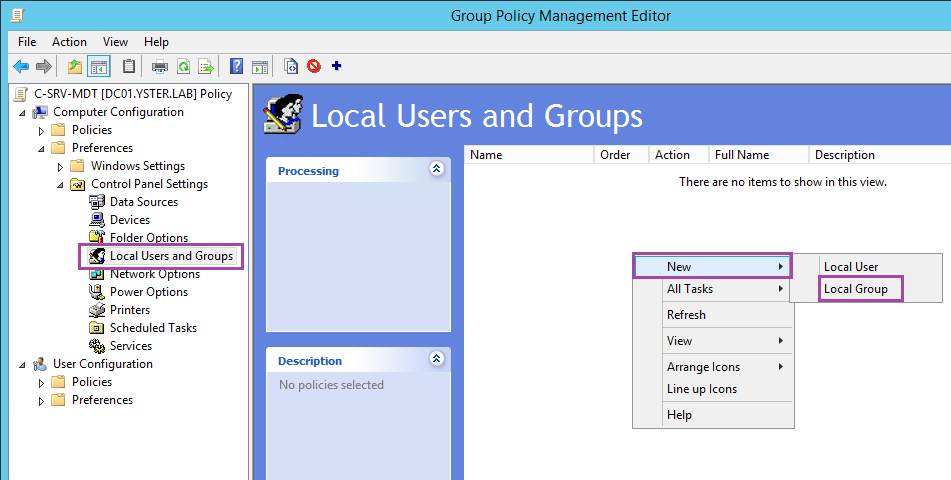
Give it an appropriate Name, then right-click on the GPO and choose Edit… Firstly, we’ll set up the local administrators group. Go to Computer Configuration – Preferences – Control Panel Settings – Local Users and Groups. Right-click on a blank area in the right-hand pane and choose New – Local Group.
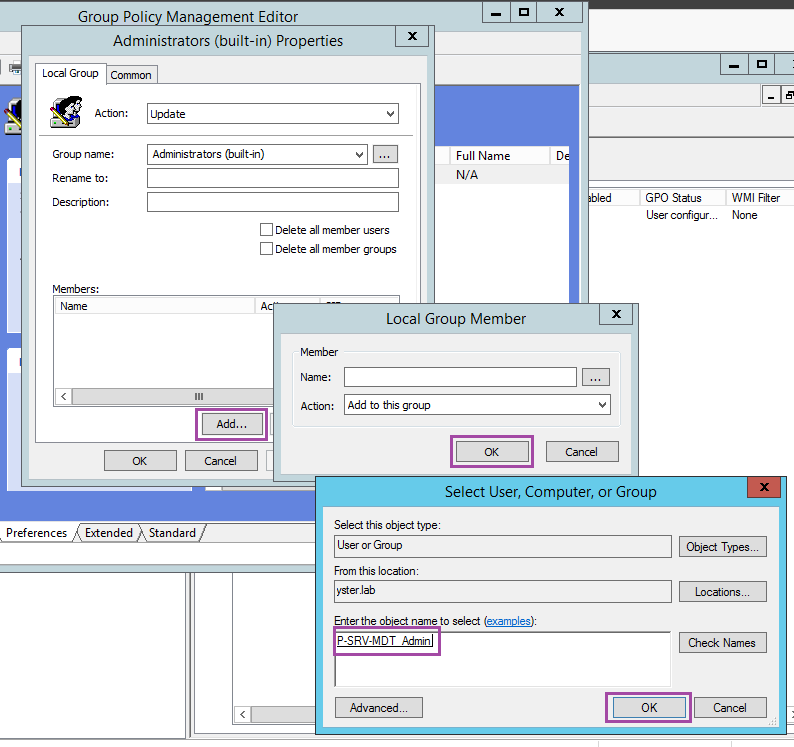
Under Group name, choose “Administrators (built-in)”. Click the Add… button and then the … button and type in the name of the Permission group for local admins that you created earlier.
Click OK a few times to save the group.
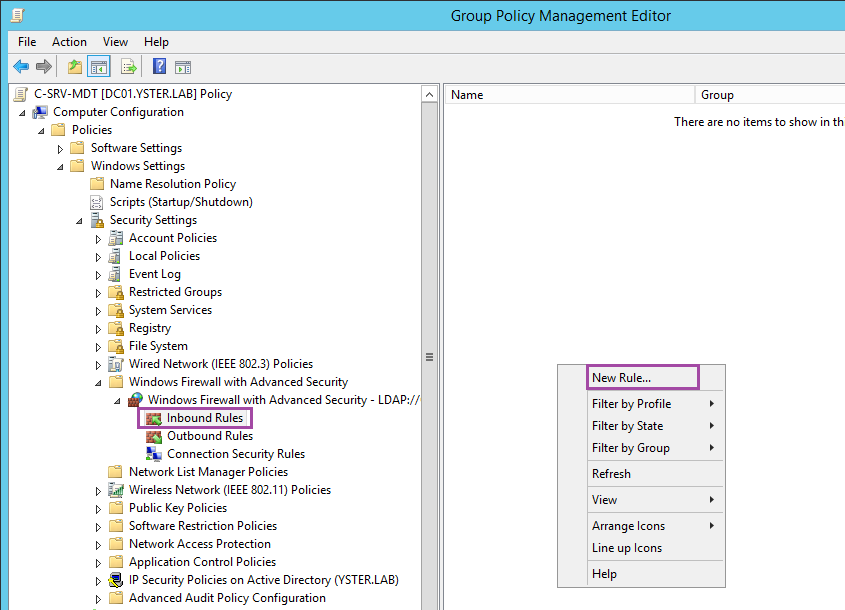
Navigate to Computer Configuration – Policies – Windows Settings – Windows Firewall with Advanced Security – Windows Firewall with Advanced Security – Inbound Rules. Right-click on a blank area in the right-hand pane and choose New Rule…
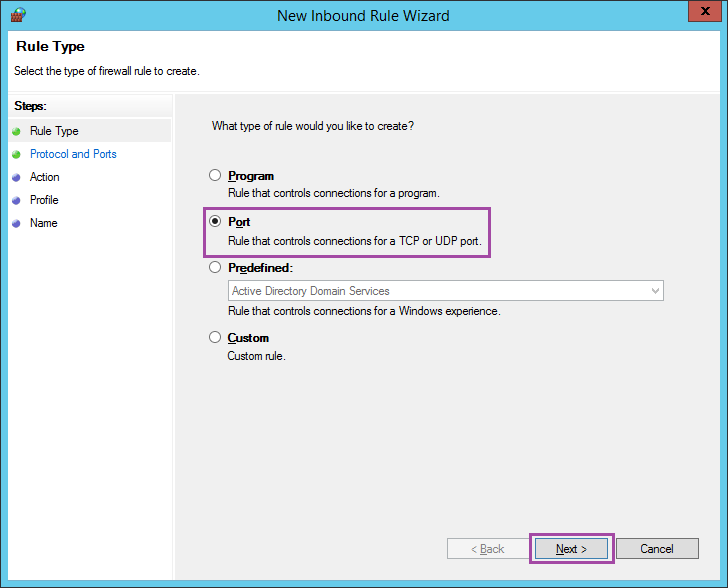
Choose Port.
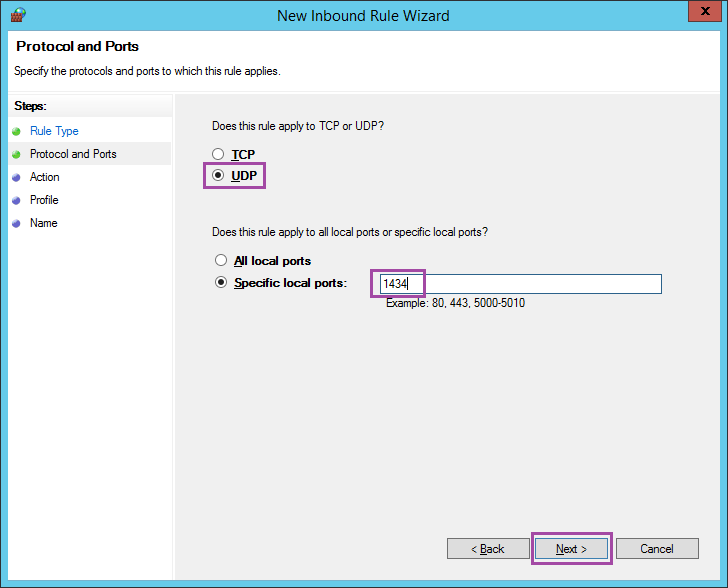
Choose UDP and enter port 1434.
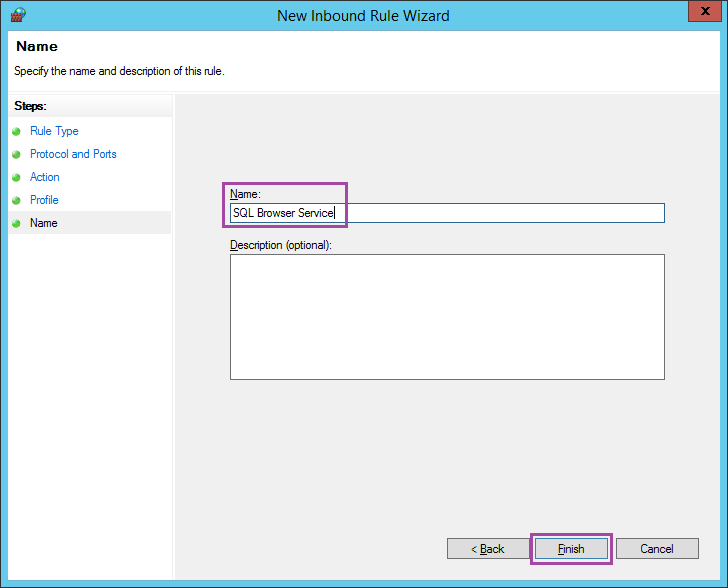
Click Next on the Action and Profile screens. Enter the Name “SQL Browser Service” and choose Finish.
Close the policy to finish.
Conclusion
This completes the initial configuration of Active Directory in preparation for the MDT software installation.
In the next post we’ll install all the prerequisite software for MDT, and perform some basic software configuration.
MDT2013 Series:
01 Intro and Active Directory Setup
02 MDT Software Installation
03 Deployment Share and MDT Database Setup
04 Network Access Permissions
05 Application and OS
06 Creating Build Task Sequence
07 MDT Database
08 WDS and PXE Booting
09 Creating the Gold Image
10 Capturing the Gold Image
11 Creating Deployment Task Sequence
12 Deployment Role and Computer Object
Hi Sean,
Amazing Guide, thank you
really good clear instructions
Appreciate all the work you put in and thank you for sharing !
Regards,
Nav
Excelent guide Sean, but let me ask something. Is really necessary install the SQL for the MDT works?
It’s not necessary no, you can do all the definitions in the INI file. However I find it much easier to work with the SQL database myself, especially when you have hundreds or thousands of machines.
Also, scripting changes to the INI file is a pain compared to the SQL db.
Thanks for the reply Sean, your tutorial its pretty good, its the most complete i’ve found in the internet. I’ll do my deployment scenario as you did (With SQL).
Keep doing the good work.